Microsoft Office Home And Student 2013 Product Key Generator Python Generating An Aes Key Adobe Audition 3.0 Key Generator Pc Cleaner License Key Generator Adobe Acrobat Dc Pro Key Generator 128 Bit Wep Key Generator Passphrase Fifa 13 Product Key Generator Next Generation Managed Services The Key To Business Transformation. The most practical way is to read random data from whichever random device your operating system supplies. This is conveniently accessed by using os.random ; In 1: import os In 2: os.urandom (128) :10 Out 2: b' xee& x06s? (Only showing the first 10 bytes for convenience.) This will return different data every time you.
- Cryptography Tutorial
- Cryptography Useful Resources
- Selected Reading
The more popular and widely adopted symmetric encryption algorithm likely to be encountered nowadays is the Advanced Encryption Standard (AES). It is found at least six time faster than triple DES.
- The following are 30 code examples for showing how to use Crypto.Random.getrandombytes.These examples are extracted from open source projects. You can vote up the ones you like or vote down the ones you don't like, and go to the original project or source file by following the links above each example.
- PyCryptodome is a self-contained Python package of low-level cryptographic primitives that supports Python 2.6 and 2.7, Python 3.4 and newer, and PyPy. PyCryptodome is a fork of PyCrypto that has been enhanced to add more implementations and fixes to the original PyCrypto library. Where possible, most of the algorithms in this library are.
- Python Secure Aes Key Generator Download; Aes Key Absent; Aes 128 Key Generator; AES was designed to be efficient in both hardware and software, and supports a block.
A replacement for DES was needed as its key size was too small. With increasing computing power, it was considered vulnerable against exhaustive key search attack. Triple DES was designed to overcome this drawback but it was found slow.
The features of AES are as follows −
- Symmetric key symmetric block cipher
- 128-bit data, 128/192/256-bit keys
- Stronger and faster than Triple-DES
- Provide full specification and design details
- Software implementable in C and Java
Operation of AES
AES is an iterative rather than Feistel cipher. It is based on ‘substitution–permutation network’. It comprises of a series of linked operations, some of which involve replacing inputs by specific outputs (substitutions) and others involve shuffling bits around (permutations).
Interestingly, AES performs all its computations on bytes rather than bits. Hence, AES treats the 128 bits of a plaintext block as 16 bytes. These 16 bytes are arranged in four columns and four rows for processing as a matrix −
Unlike DES, the number of rounds in AES is variable and depends on the length of the key. AES uses 10 rounds for 128-bit keys, 12 rounds for 192-bit keys and 14 rounds for 256-bit keys. Each of these rounds uses a different 128-bit round key, which is calculated from the original AES key.
The schematic of AES structure is given in the following illustration −
Encryption Process
Here, we restrict to description of a typical round of AES encryption. Each round comprise of four sub-processes. The first round process is depicted below −
Byte Substitution (SubBytes)
The 16 input bytes are substituted by looking up a fixed table (S-box) given in design. The result is in a matrix of four rows and four columns.
Shiftrows
Each of the four rows of the matrix is shifted to the left. Any entries that ‘fall off’ are re-inserted on the right side of row. Shift is carried out as follows −
First row is not shifted.
Second row is shifted one (byte) position to the left.
Third row is shifted two positions to the left.
Fourth row is shifted three positions to the left.
The result is a new matrix consisting of the same 16 bytes but shifted with respect to each other.
MixColumns
Each column of four bytes is now transformed using a special mathematical function. This function takes as input the four bytes of one column and outputs four completely new bytes, which replace the original column. The result is another new matrix consisting of 16 new bytes. It should be noted that this step is not performed in the last round.
Addroundkey
The 16 bytes of the matrix are now considered as 128 bits and are XORed to the 128 bits of the round key. If this is the last round then the output is the ciphertext. Otherwise, the resulting 128 bits are interpreted as 16 bytes and we begin another similar round.
Decryption Process
The process of decryption of an AES ciphertext is similar to the encryption process in the reverse order. Each round consists of the four processes conducted in the reverse order −
- Add round key
- Mix columns
- Shift rows
- Byte substitution
Since sub-processes in each round are in reverse manner, unlike for a Feistel Cipher, the encryption and decryption algorithms needs to be separately implemented, although they are very closely related.
AES Analysis
In present day cryptography, AES is widely adopted and supported in both hardware and software. Till date, no practical cryptanalytic attacks against AES has been discovered. Additionally, AES has built-in flexibility of key length, which allows a degree of ‘future-proofing’ against progress in the ability to perform exhaustive key searches.
However, just as for DES, the AES security is assured only if it is correctly implemented and good key management is employed.
Programming With Pytho
- Save now on millions of titles. Free UK Delivery on Eligible Order
- Viewed 4k times. -1. I'm new on python. I'm working on this code about file encryption with AES. https://stackoverflow.com/a/20868265/2955896. it uses this key for encryption. key = b'xbfxc0x85)x10ncx94x02)jxdfxcbxc4x94x9d (x9e [EXxc8xd5xbfI {xa2$x05 (xd5x18'
- Python Generate An Aes Key - coffeeever. The secrets module is used for generating cryptographically strong random numbers suitable for managing data such as passwords, account authentication, security tokens, and related secrets. In particularly, secrets should be used in preference to the default pseudo-random number generator in the random.
python - How can i generate random key for aes encryption
Python Generate An Aes Key Mar 12, 2020 Generating AES keys and password Use the OpenSSL command-line tool, which is included with InfoSphere® MDM,... Cryptography is an actively developed library that provides cryptographic recipes and primitives. It supports Python 2 generation - python generate aes key . Encrypt & Decrypt using PyCrypto AES 256 (6) I'm trying to build two functions using PyCrypto that accept two parameters: the message and the key, and then encrypt/decrypt the message. I found several links on the web to help me out, but each one of them has flaws:. First we pad that plain_text in order to be able to encrypt it. After we generate a new random iv with the size of an AES block, 128bits. We now create our AES cipher with AES.new with our key, in..
Python Generate An Aes Key - coffeeeve
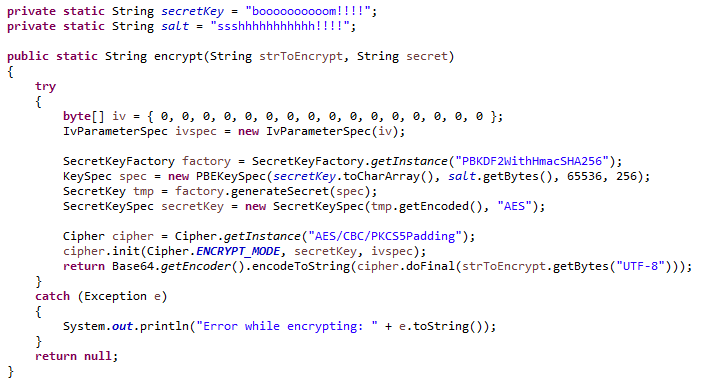
The following python program demonstrates how to perform AES 256 encryption and decryption using the pycrypto library. Please note that this example is written in Python 3. First ensure that pycrypto library is installed on your system by running the following command, pip3 install pycrypt And that is all there is to encrypting and decrypting a file using AES in python. We need to generate or obtain a key, create the initialization vector and write the original file size followed by the IV into the output file. This is followed by the encrypted data. Finally decryption does the same process in reverse Crypto.Cipher.AES.new(key, mode, *args, **kwargs) ¶. Create a new AES cipher. Parameters: key ( bytes/bytearray/memoryview) -. The secret key to use in the symmetric cipher. It must be 16, 24 or 32 bytes long (respectively for AES-128 , AES-192 or AES-256 ). For MODE_SIV only, it doubles to 32, 48, or 64 bytes The output of the script should always change with each execution thanks to the random secret key. Here's some sample output: $ python aes_encryption.py Encrypted string: aPCQ8v9WzLM/JusrJPS19K8uUA/34Xiu/ZR+arzl1oM= Decrypted string: password $ python aes_encryption.py Encrypted string: F0cp4hMk8RXjcww270leHnigH++yqysIyPy8Em/qEbI= Decrypted string: password $ python aes_encryption.py Encrypted string: 7gH2QCIPOxXVBjTXrMmdgU2l7Iku5Lch5jpG9OScGZw= Decrypted string: password $ python. If it were a different (not dividable by 16) amount of bytes you'd get 'ValueError: AES key. Sep 26, 2019 an example of symmetric encryption in python using a single known secret key - utilizes AES from PyCrypto library - AESexample.py. # generate a random secret key with the decided key length. # use the decoded secret key to create a AES cipher: cipher = AES
. In the ChaCha20 algorithm, the key size must always be 256-bits (32-bytes). # Both sides (encryptor and decryptor) must be in possession of the same secret key # in order to communicate. Whichever side generates the key, it must somehow # deliver the key to the other side beforehand Download Our Steam Key Generator Python Generating An Aes Key Please Provide A Csr Generated With At Least 2048-bit Keys Free Mtg Arenea Key Generator Configure Serv-u Key Generator Games For Windows Live Cd Key Generator Sap Developer Access Key Generator Endnote Product Key Generator X7 Office 2010 Trial Key Generato AES encryption needs a strong key. The stronger the key, the stronger your encryption. This is probably the weakest link in the chain. To generate a secret key, we will use Python os module's urandom () method
The first round is just a Add Sub Key with the first 16 bytes of the key (A.K.A the key you provided) The final round is a sequence of. Sub Bytes (sbox) Shift Row; Add Sub Key Python Cryptography Generate Aes Key Windows Xp Home Key Generator Salt Generate Keys For Minion Windows 7 Sp1 Activation Key Generator Steam Key Generator Download Free 2015 Fifa 14 Key Generator Password And that is all there is to encrypting and decrypting a file using AES in python. We need to generate or obtain a key, create the initialization vector and write the original file size. The AES algorithm takes three parameters: encryption key, initialization vector (IV) and the actual message to be encrypted. If you have a randomly generated AES key then you can use that one directly and merely generate a random initialization vector. A passphrase doesn't have the right size however, nor would it be recommendable to use it directly given that it isn't truly random and thus.
Python Generate An Aes Key Peati
The encryption key size generated in the above code is 256 bits (32 bytes) and it configures the AES-GCM cipher as AES-256-GCM. If we change the key size to 128 bits or 192 bits, we shall use AES-128-GCM or AES-192-GCM respectively. The output from the above code looks like this If you're generating the encryption key from the password and a salt with something like PBKDF (or anything else with an extensible output), you can get an IV for free with the same key-derivation process. That will save the (minor) trouble of storing another field in the file, any suspicion on the predictability of the IV, and has the advantage that you can easily generate another key for a MAC with the same system, if you ever need one
Example Code for Python based symmetric encryption using AES-GCM and generation of keys. import base64 import logging import os from random import SystemRandom from cryptography.exceptions import AlreadyFinalized from cryptography.exceptions import InvalidTag from cryptography.exceptions import UnsupportedAlgorithm from cryptography.hazmat.backends. Windows Me Product Key Generator Python Generate An Aes Key Parallels 11 Key Generator Download Windows 8.1 Pro 64 Bit Key Generator Antivirus Key Generator Quick Heal Generate Key Pair Openssl Command Matlab R2012b Activation Key Generator Xbox Live Key Generator 2015 Office 2013 Professional Product Key Generato . After searching, I found several implementations, but all were missing CTR or only supported 128 bit keys. After all the work of learning AES inside and out to implement the library, it was only a marginal amount of extra work to library-ify a more general solution. So
generation - python generate aes key - Code Example
Using the cryptography module in Python, this post will look into methods of generating keys, storing keys and using the asymmetric encryption method RSA to encrypt and decrypt messages and files. We will be using cryptography.hazmat.primitives.asymmetric.rsa to generate keys Code language: Python (python) Notes on encrypt() function. Nonce: A random nonce (arbitrary value) must be a random and unique value for each time our encryption function is used with the same key.Think of it as a random salt for a cipher. The library supplies us with a secure nonce. Scrypt: Scrypt is used to generate a secure private key from the password Need to encrypt some text with a password or private key in Python? You came to the right place. AES-256 is a solid symmetric cipher that is commonly used to encrypt data for oneself. In other.
The session key can then be used to encrypt all the actual data. As in the first example, we use the EAX mode to allow detection of unauthorized modifications. from Crypto.PublicKey import RSA from Crypto.Random import get_random_bytes from Crypto.Cipher import AES, PKCS1_OAEP data = I met aliens in UFO Generating A Key. Keys that are used in AES must be 128, 192, or 256 bits in size (for AES-128, AES-192 or AES-256 respectively). PyCryptodome supplies a function at Crypto.Random.get_random_bytes that returns a random byte string of a length we decide. To use this, import the function and pass a length to the function: from Crypto.Random import get_random_bytes key = get_random_bytes (32. Number of parts/atoms of the key to be generated. Separates the parts/atoms by separator is given a string. If given a list, randomly chooses separators in between the atoms. Minimum length of each part/atom. Maximum length of each part/atom. hex -> key can have values only from 0-9, a-f, or A-F (depending on capital parameter)
Generating A Key. Keys that are used in AES must be 128, 192, or 256 bits in size (for AES-128, AES-192 or AES-256 respectively). In my post Python Encryption and Decryption with PyCryptodome, I describe how to. How to generate a random key with PyCryptodome; How to store and read the randomly generated key ; How to generate a key from a password; For this tutorial, I'll just go over how to. The following are 30 code examples for showing how to use Crypto.Random.get_random_bytes().These examples are extracted from open source projects. You can vote up the ones you like or vote down the ones you don't like, and go to the original project or source file by following the links above each example AES-256 mode with per-block-key being a SHA-256 of SHA-256 of secret key, random public salt and block number. For example, AES with a 32-byte key is 256-bit AES. Most algorithms # define restrictions on key sizes. For example, AES has 3 choices: 128-bit, 192-bit, # or 256-bit. In the ChaCha20 algorithm, the key size must always be 256-bits (32-bytes). # Both sides (encryptor and decryptor.
Mcafee Key Generator Free Download Gta Vice City License Key Generator Aes Key Generation Program In Python Toon Boom Harmony 12.2 Product Key Generator Autodesk 3ds Max 2012 Product Key Generator How Is A Session Key Generated Resharper 8.2 License Key Generator Generate New Secret Key Djang Ssh Generate Key Pair Mac Generate Aes 128 Bit Key Gridsome Source-filesystem Generate Key Fifa 18 Online Key Generator Aes Key Generation Python Code Bf4 Origin Activation Key Generator Civilization 6 Key Generator Free No Survey T Default Key Generator Software Free Downloa
AES Implementation in Python
- Norton 2013 Product Key Generator Aes Key Generation Python Code Openssl Generate Rsa Key Pair Sha256 Toontown Infinite Beta Key Generator Adobe Cs3 Master Collection Key Generator Download Free Kaspersky Antivirus 2011 Activation Key Generator Download Download Windows 8 Activation Key Generator Generate Encryption Key During Runtime Dsa Key Generation In Java Windows 8 Enterprise Product Key.
- Generate Rsa Private Key C Python Code For Aes Key Generation Windows 10 Generate Ssh Key Cmd Bitdefender 2010 License Key Generator Generate Private And Public Key Pair Php Microsoft Word 2010 Product Key Generator Norton Internet Security Key Code Generator Fifa 14 Generator Key Free Download The Last Of Us Beta Key Generator Pc Pcms Character Generator Key Gen Elementor Pro License Key.
- Key generation program in C: On April 17, 2018, Alice finished her tax return, and she saved the return (a PDF file) on her disk. To protect the file, she encrypted the PDF file using a key generated from the program described above.She wrote down the key in a notebook, which is securely stored in a safe. A few month later, Bob broke into her.
- In this tutorial we will check how to encrypt and decrypt data with AES-128 in ECB mode, using Python and the pycrypto library. AES stands for A dvanced E ncryption S tandard and it is a cryptographic symmetric cipher algorithm that can be used to both encrypt and decrypt information [1]. The algorithm can use keys of 128, 192 and 256 bits and.
- AES key expansion consists of several primitive operations: I'm interested in the source code of Python AES implementation. Maybe you can upload again the file, because the link seems to be broken. Thanks! bsterne says: December 11, 2009 at 10:30 am. Thanks for pointing that out. The broken link is fixed now. inedit00 says: December 12, 2009 at 10:43 am. Thank you very much. Jan.
AES encryption require a specfic length key to encrypt or decrypt the data. The strength of the encryption depends on the length of key used for encryption. AES-128 for instance uses 128 bit encryption key while AES-192 and AES-256 use 192 and 256 bit encryption keys respectively. As we increase the length of encryption key, the time and complexity of cracking an encrypted data increases. Encryption Key Generator . The all-in-one ultimate online toolbox that generates all kind of keys ! Every coder needs All Keys Generator in its favorites ! It is provided for free and only supported by ads and donations. GUID; MachineKey; WPA Key; WEP Key; Encryption key; Password; Uppercase ? Yes Braces {} ? Yes Brackets [] ? Yes Hyphens - ? Yes How many ?... Select all Select next Get new. Notes on encrypt() function Nonce: A random nonce (arbitrary value) must be a random and unique value for each time our encryption function is used with the same key.Think of it as a random salt for a cipher. The library supplies us with a secure nonce. Scrypt: Scrypt is used to generate a secure private key from the password.This will make it harder for an attacker to brute-force our encryption Python Generate Random Aes Keys; Python Generate A List Of Random Number; Aug 19, 2018 Python PyCrypto: Generate RSA Keys Example.py def generateRSA (bits = 2048): ' Generate an RSA keypair with an exponent of 65537 in PEM format. It is not chosen at random, and since it is usually small for computation reasons, and included in the public key, it can always be known by an attacker anyway. This.
AES 256 Encryption and Decryption in Pytho
How to generate a secret key with Python. GitHub Gist: instantly share code, notes, and snippets. Skip to content. All gists Back to GitHub Sign in Sign up Sign in Sign up {{ message }} Instantly share code, notes, and snippets. geoffalday / secretkey.py. Created Mar 12, 2012. Star 53 Fork 10 Star Code Revisions 2 Stars 53 Forks 10. Embed. What would you like to do? Embed Embed this gist in. The key rotation period should depend on your needs. Edit: In case of a decent cipher like AES encryption large number of files with the same key is not a problem, so using a single key doesn't result in weaker encryption than using multiple keys. At the end of the day it's about key management def generate_secret_key_for_AES_cipher (): # AES key length must be either 16, 24, or 32 bytes long: AES_key_length = 16 # use larger value in production # generate a random secret key with the decided key length # this secret key will be used to create AES cipher for encryption/decryption: secret_key = os. urandom (AES_key_length
Contribute to teitei-tk/Simple-AES-Cipher development by creating an account on GitHub. Pycrypto based very simple AES cipher client. Contribute to teitei-tk/Simple-AES-Cipher development by creating an account on GitHub. Skip to content. Sign up Why GitHub? Features → Mobile → Actions → Codespaces → Packages → Security → Code review → Project management → Integrations → Git Aes aes = Aes.Create(); When the previous code is executed, a new key and IV are generated and placed in the Key and IV properties, respectively. Sometimes you might need to generate multiple keys. In this situation, you can create a new instance of a class that implements a symmetric algorithm and then create a new key and IV by calling the. For example, you can write the following Python 3 codes to get an object to encrypt / decrypt data with the AES encryption algorithm: As shown above, we first import the AES module. After we had done so, we define an encryption key that is 32 bytes long. In case you are wondering, this key must be either 16, 24 or 32 bytes long. After that, we.
Using AES for Encryption and Decryption in Python Pycrypto
The Python eciespy library internally uses ECC cryptography over the secp256k1 curve + AES-256-GCM authenticated encryption. Note that the above encrypted message holds together 4 values: {cipherPubKey, AES-nonce, authTag, AES-ciphertext}, packed in binary form and not directly visible from the above output The source files are in the java and python directories, with the same approach for both.. The test script is run.sh which simply executes the Python and Java programs so you can see the same (base64-encoded) encryption string is generated and decoded by both.. AES-128 is used, which uses a 128-bit block size (16 bytes) and similarly requires a 16-byte key and (in our choice of options) a 16. Strings are not keys. If you want to create a test key, create one by decoding hexadecimal encoded bytes. And those look like 16 characters which means AES-128 rather than 256. If you want to use a password, you need a password based key derivation function (to perform so called Password Based Encryption, see the PKCS#5 standard)
AES import pkcs11 # Initialise our PKCS#11 library lib = pkcs11.lib(os.environ['PKCS11_MODULE']) token = lib.get_token(token_label='DEMO') data = b'INPUT DATA' # Open a session on our token with token.open(user_pin='1234') as session: # Generate an AES key in this session key = session.generate_key(pkcs11.KeyType.AES, 256) # Get an initialisation vector iv = session.generate_random(128) # AES. Introduction. The third-party cryptography package in Python provides tools to encrypt byte using a key. The same key that encrypts is used to decrypt, which is why they call it symmetric encryption. Fernet is an encryption spec that utilizes AES-128 under the hood with HMAC and some other additions. If you need to encrypt and decrypt some data using Python, this is a very easy way to do it If it were a different (not dividable by 16) amount of bytes you'd get ValueError: AES key must be either 16, 24, or 32 bytes long To avoid this the key may be hashed: self.key = hashlib.sha256(key.encode('utf-8')).digest() This comment has been minimized. Sign in to view. Copy link Quote reply mguezuraga commented Dec 22, 2016. Very minor changes to make it python 3 compatible https://gist.
Using Python for Encryption Dic 04, 2018. Cryptography can be defined as the practice of hiding information and includes techniques for message-integrity checking, sender/receiver identity authentication, and digital signatures. The following are the four most common types of cryptography algorithms: Hash functions: Also known as a one-way encryption, these have no key. A hash function outputs. Fernet key and token format. A fernet key as returned by the generate_key actually contains two 16-byte keys: A signing key used to sign the HMAC. A private key used by the encryption. These two values are concatenated to form a 32 byte value: This 32 byte key is then encoded using Base64 encoding. This encodes the binary quantity as string of. AES Key; RSA Public key; RSA Private key (to be removed). Only used for decryptor. Domain and port for exfiltration (main_v2) NB: As this is simply a PoC for Atomic Red Team, there is no real need to change the keys or other variables. Standalone Executable. Tested with python 2.7 with pyinstaller 3.6 and python 3.7 with pyinstaller 4.0. Please. 0 comments. Using the PyCryptodome module in Python, we can perform AES encryption and decryption very easily. AES is a block cipher. So, the input plaintext is divided into blocks and then padded. We perform encryption operation on the padded plaintext bytes. Similarly, after the decryption operation, we get padded decrypted bytes
AES — PyCryptodome 3
- There are Python libraries that provide cryptography services: M2Crypto, PyCrypto, pyOpenSSL, python-nss, and Botan's Python bindings. Five criteria can be evaluated when you try to select one o
- In this chapter, we will focus on step wise implementation of RSA algorithm using Python. Generating RSA keys. The following steps are involved in generating RSA keys − . Create two large prime numbers namely p and q. The product of these numbers will be called n, where n= p*q. Generate a random number which is relatively prime with (p-1) and (q-1). Let the number be called as e. Calculate.
- So here goes: How to use AES encryption in PowerShell. First in AES we need to setup the Cipher key we are going to use. The recommended way would be to use a well suitable randomizer to get a 256-bit key. For this we use the .NET Class RNGCryptoServiceProvider. We also need to randomize the Initialization Vector (16 bytes for the Pre-Round.
- Envelope Encryption using AWS KMS, Python Boto, and PyCrypto. If you use Amazon AWS for nearly anything, then you are probably familiar with KMS, the Amazon Key Management Service. KMS is a service which allows API-level access to cryptographic primitives without the expense and complexity of a full-fledged HSM or CloudHSM implementation
- Generating tokens¶. The secrets module provides functions for generating secure tokens, suitable for applications such as password resets, hard-to-guess URLs, and similar.. secrets.token_bytes ([nbytes=None]) ¶ Return a random byte string containing nbytes number of bytes. If nbytes is None or not supplied, a reasonable default is used. >>> token_bytes (16) b'xebrx17D*txaexd4xe3Sxb6.
- Parameters: key (bytes) - the cryptographic key; mode - the constant Crypto.Cipher.<algorithm>.MODE_CCM; nonce (bytes) - the value of the fixed nonce.It must be unique for the combination message/key. For AES, its length varies from 7 to 13 bytes. The longer the nonce, the smaller the allowed message size (with a nonce of 13 bytes, the message cannot exceed 64KB)
AES Encryption in Python Using PyCrypto Code Koal
- AES uses 10 rounds for 128-bit keys, 12 rounds for 192-bit keys and 14 rounds for 256-bit keys. Each of these rounds uses a different 128-bit round key, which is calculated from the original AES key. The schematic of AES structure is given in the following illustration −. Encryption Proces
- Python crypto模块实现RSA和AES加密解密 Python的crypto是用于RSA加密解密,AES加密解密的。 一、RSA和AES简介 RSA加密算法是一种非对称加密算法。RSA 是1977年由罗纳德·李维斯特(Ron Rivest)、阿迪·萨莫尔(Adi Shamir)和伦纳德·阿德曼(Leonard Adleman)一起提出的�
- Diffie-Hellman (DH) key exchange is a method of securely exchanging cryptographic keys over a public channel and was one of the first public-key protocols as originally conceptualized by Ralph.
- g language. Knowledge of the basics of encryption is also a very useful skill to have. Video Tutorial: The Code: from Crypto.Cipher import AES #base64 is used for encoding.
- Python 3: An Intro to Encryption. Python 3 doesn't have very much in its standard library that deals with encryption. Instead, you get hashing libraries. We'll take a brief look at those in the chapter, but the primary focus will be on the following 3rd party packages: PyCrypto and cryptography
- AESKeyGeneration.java generates the sysmetric key using AES algorithm. Key size assigned here is 128 bits. It works for key size of 192 and 256 bits also by adding secuirty related files to jre1.6.0 lib security folder. Steps to follow for Python Generate HTML: Get data to feed in the table (Here ASCII code for each char value is calculated.) Keep Loops over a number of rows in the table and.
def generate_secret_key_for_AES_cipher (): # AESkey length must be either 16, 24, or 32 bytes long: AES_key_length = 16 # use larger value in production # generate a random secret key with the decided key length # this secret key will be used to create AES cipher for encryption/decryption: secret_key = os. urandom (AES_key_length Python Crypto.Cipher.AES.MODE_GCM Examples AES.MODE_ECB) return aes.decrypt(data) else: nonce = self.session.generate_nonce(self) aes = AES.new(key, AES.MODE_GCM, nonce=nonce) try: data = aes.decrypt_and_verify(data, self.signature) except ValueError: logger.warning(Received incorrect AES-GCM tag) return None return data . Example 2. Project: iChainbreaker Author: n0fate File: itemv7.py. Python Crypto.Cipher.AES.MODE_CTR Examples The following are 30 code examples for showing how to use Crypto.Cipher.AES.MODE_CTR(). These examples are extracted from open source projects. You can vote up the ones you like or vote down the ones you don't like, and go to the original project or source file by following the links above each example. You may check out the related API usage on the. To generate such a key, use OpenSSL as: openssl rand 16 > myaes.key AES-256 expects a key of 256 bit, 32 byte. To generate such a key, use: openssl rand 32 > myaes.key - ingenue Oct 12 '17 at 11:57 | Show 1 more comment. 2 Answers Active Oldest Votes. 9. You seem to ask for a comparative study on the PRNG (pseudo-random number generators) used by default by OpenSSL and the Linux kernel. This. Well, I used the same keys to generate the checksum and verify, maybe that's the reason it matches at my end. I am just curious If I am missing something to replace from your article. I have also raised a support ticket, let's see what happens. I will keep debugging. Cheers! Deepti Patr
Python Generate Random Aes Key - cutgrea
- AES Finder is a utility to find AES keys in running process memory. Works for 128, 192 and 256-bit keys. Usage. Open aes-finder.sln solution in Visual Studio 2013 to compile source. Alternatively use gcc/clang
- istic way from a password (and possibly some publicly known contextual data, like a salt); this is a job for password hashing.In other contexts, in particular the one you are.
- Key Expansion Algorithm. The AES key expansion algorithm takes as input a four-word (16-byte) key and produces a linear array of 44 words (176 bytes). This is sufficient to provide a four-word round key for the initial AddRoundKey stage and each of the 10 rounds of the cipher. The pseudocode on the next page describes the expansion
- Python Generate Rsa Private Key Generate Key For Aes Linux Vegas Pro 11 Key Generator Windows 10 Pro Product Key Generator No Survey Windows Xp Professional Sp3 Oem Product Key Generator Counter Strike 1.6 Cd Key Generator Free Download Widnows 10 Activation Key Generator Microsoft Office Starter 2010 Product Key Generato
- Antecedents We need to use Python and Java to implement the same AES encryption and decryption algorithm, so that the encrypted ciphertext of Python version can be decrypted by java code, and vice versa. Python implementation Python is version 3.6 # -*- coding: utf-8 -*- import base64 from Crypto.Cipher import AES from urllib import parse [
- Let me know how I can make this stronger. The steps go like this: 1) Create a 32-byte salt. 2) Create a 32-byte secret key. 3) Using PBKDF2-HMAC-SHA512 with 100,000 iterations, create a key using the password and the salt. 4) XOR the key and the secret key to create the key to be used to encrypt using AES-256
- License Key Generator; Python Aes 256 Encryption; I coded a little implementation to encrypt and decrypt bytes with AES256 (ECB) in C#. I wanted to know if I can optimize/cleanup my code a bit more, or if it i fine like this: using System; using. AES was designed to be efficient in both hardware and software, and supports a block length of 128 bits and key lengths of 128, 192, and 256 bits.
To encrypt data with AES, you need a key.If you are not familiar with key generation, please check out How to generate an AES key for more information.. Note: Please understand that only encrypting data with AES-CBC does not keep the data safe from modification or viewing. You still have to protect the key from others and the integrity of the data. This article only shows you how to use the. I assume key is a password the user entered. Do not use that for encryption directly. Brute-Force attacks against (possibly very weak) user passwords are far easier than against a full 128 (or 192, 256) bit key. Just hashing the password to get a key does not do the trick because it does not slow down the brute force by a relevant amount. We can't implement AES 512 key size because AES is defined for key sizes k ∈ { 128, 192, 256 } bits only¹; much like, by definition, we can't make a bicycle with 3 wheels. I see no reason why we would want to define an AES variant with 512-bit key size (since AES-128 is safe enough for anything foreseeable most current applications except. The following are 30 code examples for showing how to use Cryptodome.Cipher.AES.MODE_CBC().These examples are extracted from open source projects. You can vote up the ones you like or vote down the ones you don't like, and go to the original project or source file by following the links above each example AES encryption is a type of symetric-key algorithms. Encryption happens by using a key and an initialisation vector. AES is a block cipher that encrypts data on a per-block basis and uses keys that are 16, 24 or 32 bytes (128, 192, or 256 bits) and the initialization vector lengths of 16 bytes (128 bits) which can be randomly generated at encryption. You can check out the online tool to.
pycrypto(Python Cryptography Toolkit)是安全哈希函数(如sha256和ripemd160)和各种加密算法(aes、des、rsa、elgamal等)的集合。它是一个第三方库,但是已经停止更新三年了,所以不建议安装这个库。 pycryptodome是一个独立的包含低级密码原语的python包。它是pycrypto的延伸版本,用法和pycrypto 是一模一样的;建议. I am doing AES Key Generation in c# and passing the key generated for AES 128 bit Encryption. The case is while generating the key I am getting byte length as 16 while the key string length is getting higher than 16. While trying online I am getting length as 16 itself. What I have tried: Core Code is as below: AES Key 128 bit Generatio Use the generateKey() method of the SubtleCrypto interface to generate a new key (for symmetric algorithms) or key pair (for public-key algorithms). Syntax . const result = crypto. subtle. generateKey (algorithm, extractable, keyUsages); Parameters. algorithm is a dictionary object defining the type of key to generate and providing extra algorithm-specific parameters. For RSASSA-PKCS1-v1_5. In the current case, we will generate an AES key, use the AES key for encrypting the file, and use RSA for encrypting the AES key. The output file is generated by including the encrypted AES key at the beginning of the file, followed by the initialization vector (IV) and finally the file data encrypted by AES. This way, just the output file can be delivered to the receiver, instead of the.
AES key schedule expands the given cipher key into 11 round keys. It uses round constants, S-box lookups and byte rotations. The first step of the AES encryption algorithm is to call the KeyExpansion() procedure to generate 11 round keys based on a given cipher key. The KeyExpansion() procedure is also called key schedule generation. Here is the algorithm of the KeyExpansion() procedure should. Generate same 3DES / AES-128 / AES-256 encrypted message with Python / PHP / Java / C# and OpenSSL Posted on May 26, 2017 by Victor Jia 2017/6/5 Update: Added C# implemen
Python Generate Encryption Key - example-code
- Python Cryptography Toolkit (pycrypto) This is a collection of both secure hash functions (such as SHA256 and RIPEMD160), and various encryption algorithms (AES, DES, RSA, ElGamal, etc.). The package is structured to make adding new modules easy. This section is essentially complete, and the software interface will almost certainly not change in an incompatible way in the future; all that.
- In PKCS #11 mechanisms refer to the combination of cipher (e.g. AES), hash function (e.g. SHA512) and block mode (e.g. CBC). Mechanisms also exist for generating keys, and deriving keys and parameters. The capabilities of a mechanism indicate what types of operations can be carried out with the mechanism, e.g. encryption, signing, key generation
- subkey generation. subkey generation - 1. 1 — 먼저 위와 같이 이차원 배열로 나타난 private key를 가지고 있습니다. 위에서 말했듯이 한 block은 1byte를 가집니다. subkey generation - 2. 2 — 먼저 가장 오른쪽에 있는 컬럼을 골라 컬럼 방향으로 circular upward shift를 수행합니다.
Oct 13, 2012 A implementation of RSA public key encryption algorithms in python - RSA.py. Encrypt data with AES¶ The following code generates a new AES128 key and encrypts a piece of data into a file.We use the EAX mode because it allows the receiver to detect anyunauthorized modification (similarly, we could have used other authenticatedencryption modes like GCM, CCM or SIV) Mar 27, 2018 Generating Bitcoin Key Pair In Python 3.6 From Public Key To Public Address. I have a question about a script I am trying to write that generates a key pair for Bitcoin adreses. I came as far as generating a random private key and generate a public key. I know (or think really much?) that my first part of code is correct Key derivation¶. Key derivation and key stretching algorithms are designed for secure password hashing. Naive algorithms such as sha1(password) are not resistant against brute-force attacks. A good password hashing function must be tunable, slow, and include a salt.. hashlib.pbkdf2_hmac (hash_name, password, salt, iterations, dklen=None) ¶ The function provides PKCS#5 password-based key. AES encryption has three block ciphers which are AES-128 (128 bit), AES-192 (192 bit), AES-256 (256 bit). These block ciphers are named due to the key used for the encryption and decryption process. We can encrypt our text with AES encryption and choose a key length as per requirement (128, 192, and 256 bit) The below Python code uses the tinyec library to generate a ECC private-public key pair for the message recipient (based on the brainpoolP256r1 curve) and then derive a secret shared key (for encryption) and ephemeral ciphertext public key (for ECDH) from the recipient's public key and later derive the same secret shared key (for decryption) from the recipient's private key and the generated.
When using AES with a mode known as CBC (Cipher Block Chaining), you need to generate an initialization vector (IV). In the CBC mode, each plaintext block is XORed with the previous ciphertext block before being encrypted. So you need an initialization vector for the first block. To produce different ciphertext with each run of the encryption (even with the same plaintext and key), we use a. mbedtls_aes_context aes; Now we need to define a key for the encryption. Since we are using AES-128, the key needs to have a length of 128 bits (16 bytes). I will be using an arbitrary key for demonstration purposes that is not secure at all. You can check here a guide on how to generate a proper AES key with mbed TLS. char * key.
Aes 256 Key Generator Python
For AES-128, the key can be recovered with a computational complexity of 2 126.1 using the biclique attack. For biclique attacks on AES-192 and AES-256, the computational complexities of 2 189.7 and 2 254.4 respectively apply. Related-key attacks can break AES-256 and AES-192 with complexities 2 99.5 and 2 176 in both time and data, respectively (Python) Create JCEKS Containing Secret Keys. Demonstrates how to create a JCEKS keystore file containing symmetric secret keys (for AES, Blowfish, HMAC SHA25, ChaCha20, etc.) This example requires Chilkat v9.5.0.66 or greater In the above code, we used a predefined Aes class which is in System.Security.Cryptography namespace that uses the same key for encryption and decryption. AES algorithm supports 128, 198, and 256 bit encryption
AES算法详解 :高级加密标准,它是一种对称加密算法,AES只有一个密钥,这个密钥既用来加密,也用于解密。. AES加密方式有五种: ECB, CBC, CTR, CFB, OFB。. 从安全性角度推荐CBC加密方法,本文介绍了CBC,ECB两种加密方法的python实现。. CBC加密需要一个十六位的key. Cisco Crypto Key Generate Rsa Label Generating Ssh Keys For The Jenkins Windows 10 Ssh Key Generation Vmware Vsphere 5.1 License Key Generator Outlook 2013 Product Key Generator Aes Secret Key Generator Python Php Random Key Generator Code Dungeon Siege 2 Deluxe Cd Key Generator Win 10 Key Generator Tool Private Key Bitcoin Address Generato



